GCP is a public cloud vendor like competitors of Azure and AWS. Customers are able to access server resources housed in Google's data centers around the world on a pay-per-user basis.
GCP offers a suite of computing services to do everything from Cost management to data management to delivering web and video over the web to AI and machine learning tools.
Google's global infrastructure has given 24X7 services around the world with highest speed and reliability. GCP starts with a region and within a region are availability zones. These availability zones are isolated from a single point of failure. Some resources such as HTTP global load balancer are global and can receive requests from any of the Google cloud Edge locations and regions. Others resources like storage can be regional. The storage is distributed across multiple zones within a region for redundancy.
We need to select the locations depending on the performance, reliability and scalability and security needs of your organization.
Plan to create a GCP setup:
Cloud Shell:
GCP includes command line tools for Google cloud product and services:
GCP includes command line tools for Google cloud product and services:
gcloud - Main CLI for GCP cloud
gsutil - Cloud storage
bq - biq query
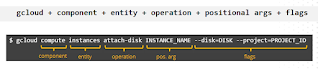
Sytex of gcloud:
gcloud + component + entity + operation + positional args + flags
- Policies are inherit from top to bottom approach, There is a no ways to remove the permission that was grant at the top level into resource level.
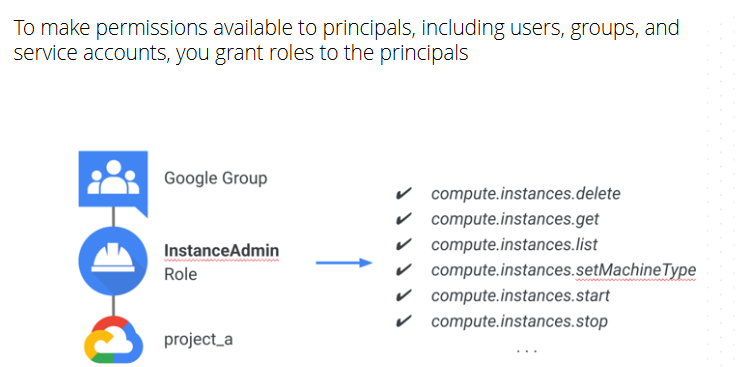
Different types of Roles in GCP:
- Basic Role - Owner, Editor and view
- Predefined Role - Service specific role [pub/sub subscriber]
- Custom Role - Based on user specified list of permission
We can create a service account for automation of manual task. We can able to create a service account through GUI or glcoud CLI.
#gcloud compute instances create myinstance --service-account servicename
Create a service account for PubSub subscription
#gcloud pubsub subscriptions create [subscription_name] --topic [Topic_name] --push-endpoint=[Cloud_Run_Service_URL] --push-auth-service-account=[serviceacountname]@prjectid.iam.gserviceaccount.com
Best practice of Access Management:
- Donot grant a basic roles [Owner, Editor, viewer]
- Have more than one organization admin
- Grant roles to Google groups instead of individuals
- Be cautious when granting the Service Account user role
- Regularly check Cloud Audit logs and audit IAM policy changes.









![Terraform [HCL] Language - Write a terraform code](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgPHNB41WPXEDjV9LeFXHGhFjIdb4hvuNX81Vz3BL9hepo8Vfxx7cyI-cWcB3OhdneskZ7T2Mh9ySNbfzy_pBnYcZC42PZ9ZsD2SuO3jaDw5a4uCUcCi1brN5TvL54EfVAfpEJNrqwLmfWc5Lg9gbepYzwjhhNEkGxSLy5j0mr-Y9P0GvaeSld6Kl0jExk/w72-h72-p-k-no-nu/Terraform.png)


















No comments:
Post a Comment